The Ultimate Choice For your Digital Security > Blog > cybe threats > Threats found in LAN-T0-WAN Domain in Typical IT Infrasstructure
Threats found in LAN-T0-WAN Domain in Typical IT Infrasstructure
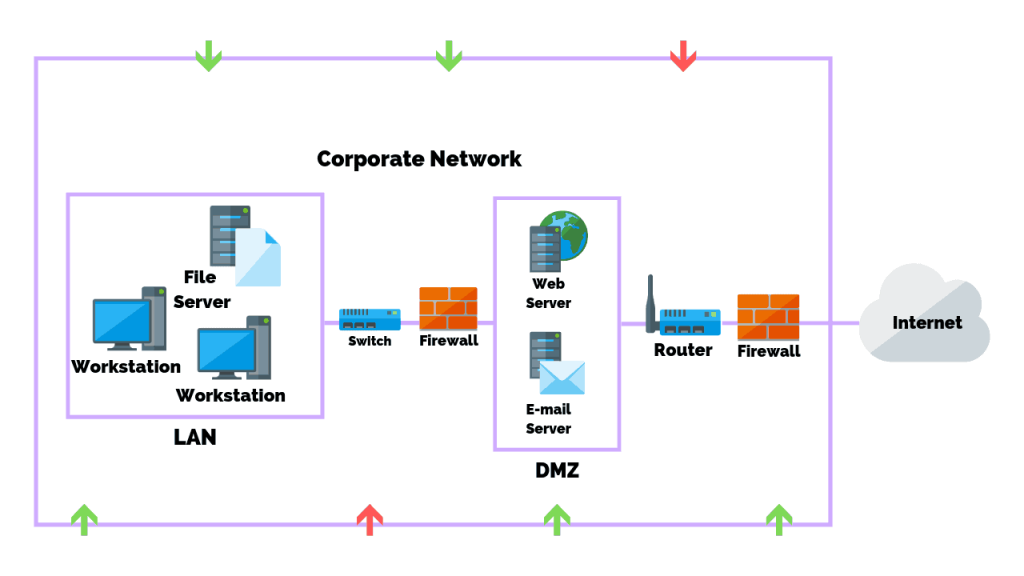
The LAN-to-WAN domain is where the IT infrastructure links to a wide area network and the internet. This acts as the connecting point that provides internet access for the entire organization. As we all know internet connectivity comes with its benefits as well as drawbacks since it is open, public, and easily available by anyone. The devices in this domain need strict security controls as they are open to public as per design and can act as gateways into the controlled LAN environment. Examples of devices/applications in this domain include your Router, Proxy Servers, any machines located in the DMZ (Demilitarized Zone) and security IDS/IPS Systems. The following threats are associated with this domain.
- Unauthorized access through the LAN-to-WAN domain refers to where an attacker could gain control of an organization through the evasion of security controls like IDS/IPS or firewall system through malicious traffic.
- Unauthorized network probing and port scanning is when a malicious actor attempts to scan publically facing IP addresses to learn the state of the network by checking active IP addresses and opened ports. If an open port is discovered he tries to use that to gain access. like ssh, he can do brute forcing
- Denial of Service attacks on external public-facing IPs and internet link a perpetrator could send large chunks of traffic to disrupt normal operations and make network resources unavailable to its intended, users. the DDos could be targetted on both physical devices or logical eg Routers, IDs, or Ports
- Unkown email attachments and embedded URL links Local users can receive malware embedded documents from the internet and when opened they implant malware on their machine the same applies to evil URL links that when clicked they execute backdoor on the victim side to gain access without the user knowing.
- Data Leakage: This is a major risk in the domain and can happen due to a malicious insider or accidentally. Technologies like deep packet scanning firewalls will allow you to detect some of these data transfers if configured correctly. One example configuration would be to block any transfer of a file with a particular data classification over file transfer protocols & email.
- A misconfiguration on the network devices if LAN devices facing the internet are misconfigured they could create channels that bad guys can use or leverage to access internal applications
- Hardware Failures/Physical threats: All devices and hardware in this domain need to be protected from Physical threats like hardware failure, fire, natural disasters, water with properly configured failover/backup systems, and adequate security like fire protection/suppression systems and waterproofing.
- Viruses, Trojans, Worms & Ransomware: Since the domain is a gateway to the wider internet there is a major threat of viruses, ransomware, etc that can infect the internal network if not actively protected against. All files transferred through the endpoints should be scanned for malicious code & viruses and quarantine procedures setup for unknown files. Access to known malicious sites should be blocked at this level as well.
